- New Forcepoint Converged Security Platform delivers extensible and behavior-based risk-adaptive protection to accelerate digital transformation for enterprises and government agencies
- Forcepoint Dynamic Edge Protection, the first solution on the new converged platform, modernizes networks for cloud adoption and delivers advanced user, data, network and web security
- Strategic investment in global partner ecosystem extends Forcepoint’s risk-adaptive cybersecurity through integrated solutions with leading technology providers such as Amazon Web Services (AWS), IBM Security, Microsoft, Citrix, Boldon James, Ping Identity, Seclore and more
Forcepoint is strategically investing in the creation of a human-centric technology partner ecosystem that enables customers to achieve their digital transformation outcomes by enabling secure migration of data, applications, and business operations to the cloud.
Forcepoint’s global technology and strategic alliances span areas including public cloud, data classification, identity and access management. It ensures that customers have the ability to simplify collaboration between vendors and create an integrated security stack. Forcepoint ensures that all tools including identity-as-a-service tools, collaboration, HR, IT service management, workflows, incident response and other mission-critical business applications can deliver an understanding of the behavior of digital identities, and help extend the risk-adaptive protection to existing security infrastructure.
About Cloud Security
The widespread adoption of cloud solutions has been driven by the myriad of associated benefits offered, such as flexibility, scalability and remote access. At the same time, concerns have been raised regarding the security of these solutions when it comes to keeping sensitive data safe from malicious actors.
Fortunately, this can be avoided by demonstrating that both the organisation and the provider are committed to optimum cybersecurity, by investing in adequate prevention of cyber threats, good data security and data protection. Forcepoint Cloud Security Solution addresses these concerns
At the recent Bankers Summit in Lagos Nigeria, Forcepoint Regional Manager for Africa – Gregg Brans noted that “Forcepoint’s security solutions help customers transition from on-premise to cloud mitigatingany cloud adoption fears.We integrate perfectly with public cloud service providers like AWS, Azure, G-Suite providing a secure risk-adaptive intelligent approach to security challenges.”
Our journey into a complex world of digital transformation is already happening . Our ecosystems are already beginning to look the one on the top right. Complexity and risk is already high, as we operate in a multi-dimensional world based, on user and data connections.
- 73% of enterprises will run almost entirely on SaaS by 2020
- 87% of companies rely on their employees using personal devices to access business apps
- 2.5 quintillion bytes of data are created each day
Organizations need to place users and data at the center of their design thinking
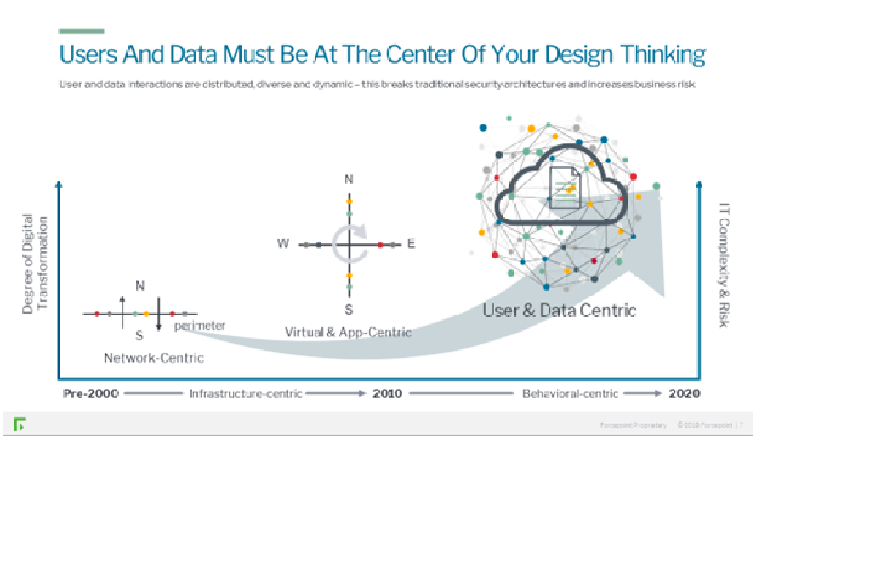

Human-centric cyber security from Forcepoint flips that paradigm on its head and changes everything. By making humans, and not events, the units of analysis, you can now use events as data input to understand what each individual is trying to do by their behavior.
Based on that understanding of each user’s behavior and intent, you can then apply different policies depending on the riskiness of that behavior. The result is one to one security which provides more user freedom and appropriate security enforcement based on a risk adaptive profile.
Human-centric cyber security flips that paradigm on its head and changes everything. By making humans, and not events, the units of analysis, you can now use events as data input to understand what each individual is trying to do by their behavior.
Based on that understanding of each user’s behavior and intent, you can then apply different policies depending on the riskiness of that behavior. You can now get aggressive with automation to stop threats without breaking the environment. The result is ONE to ONE security that provides more user freedom and appropriate security enforcement based on a risk adaptive profile
Forcepoint Human-centric Portfolio
Forcepoint is converging its capabilities to simplify deployment and management of your security stack and eliminate security gaps. Each capability is best-in-class; you can start anywhere and expand as your needs grow. Forcepoint`s unified policy and common analytics and orchestration streamline management.
Forcepoint’s solutions include:
Forcepoint DLP
Discovery and protection to meet regulatory and industry compliance.
Forcepoint Behavioral Analytics
User and entity behavior analytics for a zero-perimeter world. The leader in actionable insights based on risk-adaptive scoring.
Forcepoint Insider Threat
User visibility and incident context for sensitive data. The most comprehensive understanding of user intent, trusted on over 1 million endpoints.
Forcepoint CASB
Visibility and control over your complete cloud environment. The broadest cloud application support with unique customized risk assessment based
Forcepoint SD-WAN & Next Generation Firewall (NGFW)
Highly secure, efficient and available network security. Cuts network expenses by 50 percent, reduces cyberattacks by up to 86 percent and slashes incident response time by as much as 73 percent.
Forcepoint Data Guard
Secure collaboration and information sharing for government agencies. Eliminates costly and time-consuming manual data transfers of highly-regulated, sensitive data.
Forcepoint Web and Email Security
Unified protection from advanced threats at any location, on any device. Threat detection is 100 percent with zero false positives.














































